Because it powers one-third of all websites on the internet, WordPress also absorbs an unequal share of attacks. In fact, 83 percent of websites affected in 2017 were powered by the popular CMS.
This doesn’t mean that WP is in and of itself insecure.
Largely, it’s a numbers game when you’re the most popular and oft-used platform, favored by mommy bloggers and Fortune 500 companies alike. The trick is to know where the WordPress vulnerabilities lie and how to strengthen your website protection against hacking, hijacking, and unintentional data leaks.
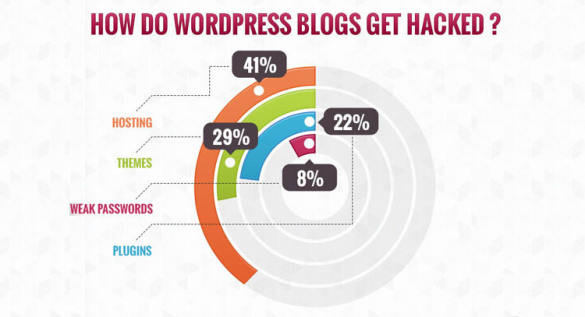
There are five major areas that WordPress admins and website owners should monitor: front-end access points, admin dashboards, WP databases, hosting platforms, and themes/plugins.
Without further ado, here is our comprehensive 2019 guide to WordPress security.
Access Points to Maintain Website Protection
Sometimes the quickest way to infiltrate a website is right through the front door. People log in on public networks and forget to log out, devices are lost or stolen, or passwords are too easy. These are attractive circumstances for trouble makers. WordPress security plugins and features provide you with the ability to customize access and keep bad actors out. You can also restrict access by using a password manager to create and store secure, unique passwords and using 2FA authentication to limit access.
There are also some built-in measures you can take like setting an automatic function that logs out idle users and a lock-down mechanism that locks the website down and sends you an alert when someone attempts the wrong password too many times.
If a hacker knows the direct login URL, they can try dipping into their Guesswork Database of commonly used passwords and combinations. This can be prevented by changing the login URL to something like my_new_login or my_new_admin.
WordPress also has a security audit log plugin. It monitors a range of activities and issues reports as well as alerts when it detects unusual activity.
Some of the reports include:
– Content, URL, or custom field alterations
– Tag and category changes
– Widget and menu changes
– User changes such as profiles, logins, activities, email, and usernames
– WordPress core and settings alterations
– WordPress multisite network discrepancies
Administrator Dashboards
One of the great things about WordPress is that the open source nature atmosphere allows experienced coders to customize. Because the admin login page is well-known, it’s a favorite target for brute force attacks. One simple fix is to alter the domain name by adding /wp-login.php or /wp-admin/ to the URL. However, the first thing you should do is change the default user name from “admin” to something unique and hard to guess. Some suggest using your email address as a user name, but if it’s publicly posted anywhere, that just makes it easier to hack.
You should also encrypt your admin panel using secure sockets layer (SSL). These can be purchased from a trusted third-party provider if it isn’t available at no cost through your hosting service. Adding an SSL certificate to your blog will also help you rank higher in the SERPs and assure your website protection.
Brute Force Attacks
Brute force attacks are a method of using trial and error to crack passwords and other access points with malicious intent. They are used to insert malicious coding, strain system resources to crash websites, or just steal sensitive information. They can even be used to lock you out of your admin panel and hold your website hostage.
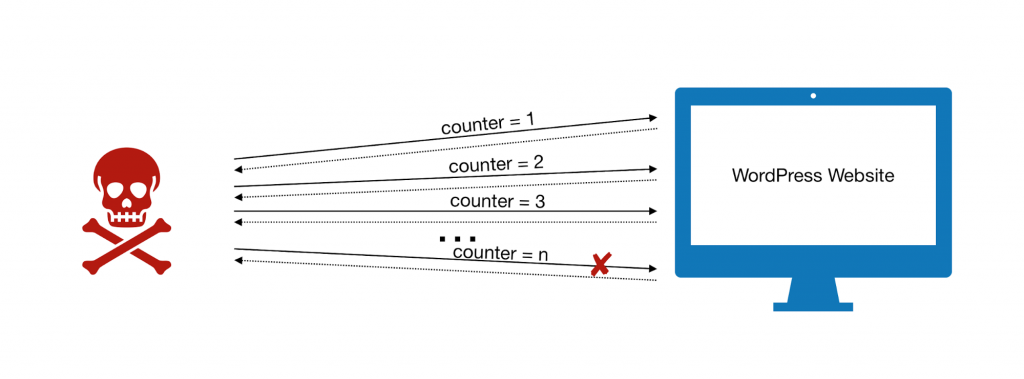
Many of the measures we’ve suggested will prevent DDoS attacks, spoofing, and other hacktivity. Here are some more ideas that are specifically designed for these types of security issues.
1. Use firewalls. WP developers have created a few good ones; Sucuri is one of the best. You install them at the application level and the DNS level.
2. Add a password or use 2FA authentication on your host server in addition to the access points to the website itself.
3. Disable directory browsing. Some hackers browse admin directories to probe for weak points. There’s a pretty easy fix for that. Just add the line “Options – Indexes” at the end of your .htaccess file.
4. Disable PHP file executions in folders that don’t require .php to function. Just create this command line in a text editor:
<Files *.php>
deny from all
</Files>
Then, save it as a .htaccess file, and upload it to your /wp-content/uploads files with an FTP client.
Did you know that if a hacker knows your WP version number, they can customize an attack? You can remove your version number from your website by manually adding the following code provided by WP Beginner to your functions.php file:
function wpbeginner_remove_version() {
return ”;
}
add_filter(‘the_generator’, ‘wpbeginner_remove_version’);
Hosting Platforms
The ratio of uptime/downtime is behind many WordPress vulnerabilities. If you don’t know your provider’s numbers, find out. This real-time web host comparison of uptimes lets you compare yours to the 99.9 percent standard that serious industry players should hit. Solid performance in this area is not just for making site visitors happy. Downtime is an open invitation for a hacker to breach the server or might be an indication they’re already there. Be suspicious of free or ultra-cheap web services. They usually don’t invest in the latest technology and like to add on hidden fees.
Backups are another critical area. Some hosting services offer system backups, but you need to ask your provider:
– Do you backup your system?
– How often do you perform backups?
– What is backed up, and how/where is it stored?
– Do clients have access to the backups?
– Is there a mechanism to restore websites?
Even if your hosting service does provide backups, and you’re allowed access, it’s still better to perform your own. You can store them on-site or use an independent cloud storage service.
Plugins and Themes
Third-party plugins and themes are notorious security risks. It’s not so much that the creators intentionally make them insecure. The problem is we experiment with different layouts and functions, and then just leave unused or old plugins and themes lying around in a database or file. Make sure that you install updates for your themes and plugins as soon as they’re available, or choose automatic updates if that feature is available with your theme or plugin. Uninstall any that are obsolete, have no support, and those you no longer use.
Additionally, if you’re not up-to-speed with the seismic change in regard to how you should collect and handle customer/visitor data on your website, do yourself a favor and use a theme like Newspaper or Newsmag. Both have been vetted by the top industry influencer, the Envato ThemeForest Market and support the new international privacy regulations known as GDPR.
In fact, don’t use any theme or plugin that hasn’t been thoroughly tested for security vulnerabilities in order to fend off exploits that plague other, less well-designed, plugins and themes. It’ll save you a lot of headaches down the road and will keep website protection at a high level.
Final Thoughts
Like most popular entities, WordPress sites are a regular target for malicious actors, but don’t let the open source flexibility fool you. WordPress is no less secure than other website builders and platforms. Most problems with security can be chalked up to the human error and lack of due diligence. If you need help in maintaining your WordPress website, you could get quick and efficient assistance from the Fix Runner team.
While we can’t completely eliminate threats, but we can minimize risk by taking precautionary measures. Using security best practices will help ensure your website protection and that your visitors continue to enjoy your content with fewer concerns about hacking, cracking, or leaks.